1. Introduction & Overview
What is OLTP?
OLTP (Online Transaction Processing) refers to a class of systems that manage transaction-oriented applications, typically for data entry and retrieval processes. OLTP systems are characterized by a large number of short online transactions (INSERT, UPDATE, DELETE).
- Primary Goal: Ensure fast query processing while maintaining data integrity in multi-access environments.
- Example: Banking systems, order entry, retail sales.
History or Background
- 1970s: Emerged with the advent of relational database systems (IBM’s System R).
- 1980s–1990s: OLTP systems matured with Oracle, SQL Server, and PostgreSQL.
- Modern Day: OLTP is foundational in microservices, Kubernetes-based architectures, and real-time DevSecOps pipelines.
Why is it Relevant in DevSecOps?
OLTP systems are vital in DevSecOps for:
- Real-time telemetry and logging
- Security monitoring and compliance auditing
- Supporting transactional microservices with auditability
- Quick rollback and recovery capabilities
2. Core Concepts & Terminology
Key Terms and Definitions
| Term | Definition |
|---|---|
| ACID | Set of properties (Atomicity, Consistency, Isolation, Durability) ensuring reliable processing. |
| Transaction | A single unit of work that must either complete entirely or not at all. |
| Concurrency | Multiple transactions occurring at the same time without interference. |
| Isolation Levels | Defines the degree to which a transaction must be isolated from others. |
| Rollback | Undo all changes if a transaction fails. |
| Commit | Save all changes of a successful transaction permanently. |
How it Fits into the DevSecOps Lifecycle
| DevSecOps Phase | OLTP Role |
|---|---|
| Plan | Define transactional logging requirements. |
| Develop | Embed OLTP code into microservices. |
| Build | Integrate OLTP schema migrations in CI/CD. |
| Test | Perform ACID compliance and security validation. |
| Release | Track deployment metrics and rollback options. |
| Operate | Monitor transactional health in real-time. |
| Secure | Audit every transaction for compliance. |
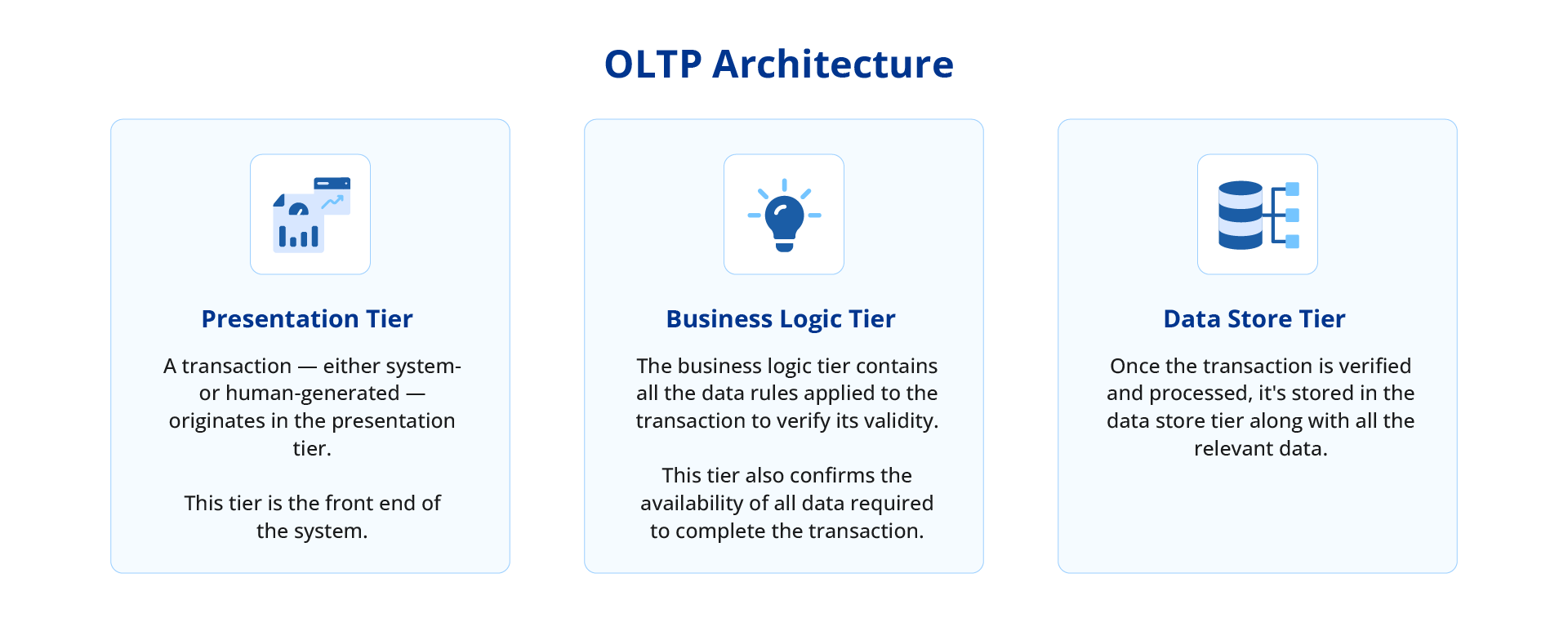
3. Architecture & How It Works
Components
- Client Applications: Interfaces for initiating transactions (APIs, UIs).
- Transaction Manager: Orchestrates transactional rules and commits.
- Database Engine (RDBMS): Executes SQL commands with ACID guarantees.
- Storage Engine: Handles data persistence and indexing.
- Concurrency Controller: Ensures isolation and prevents race conditions.
- Logging/Audit Module: Records transactions for traceability and rollback.
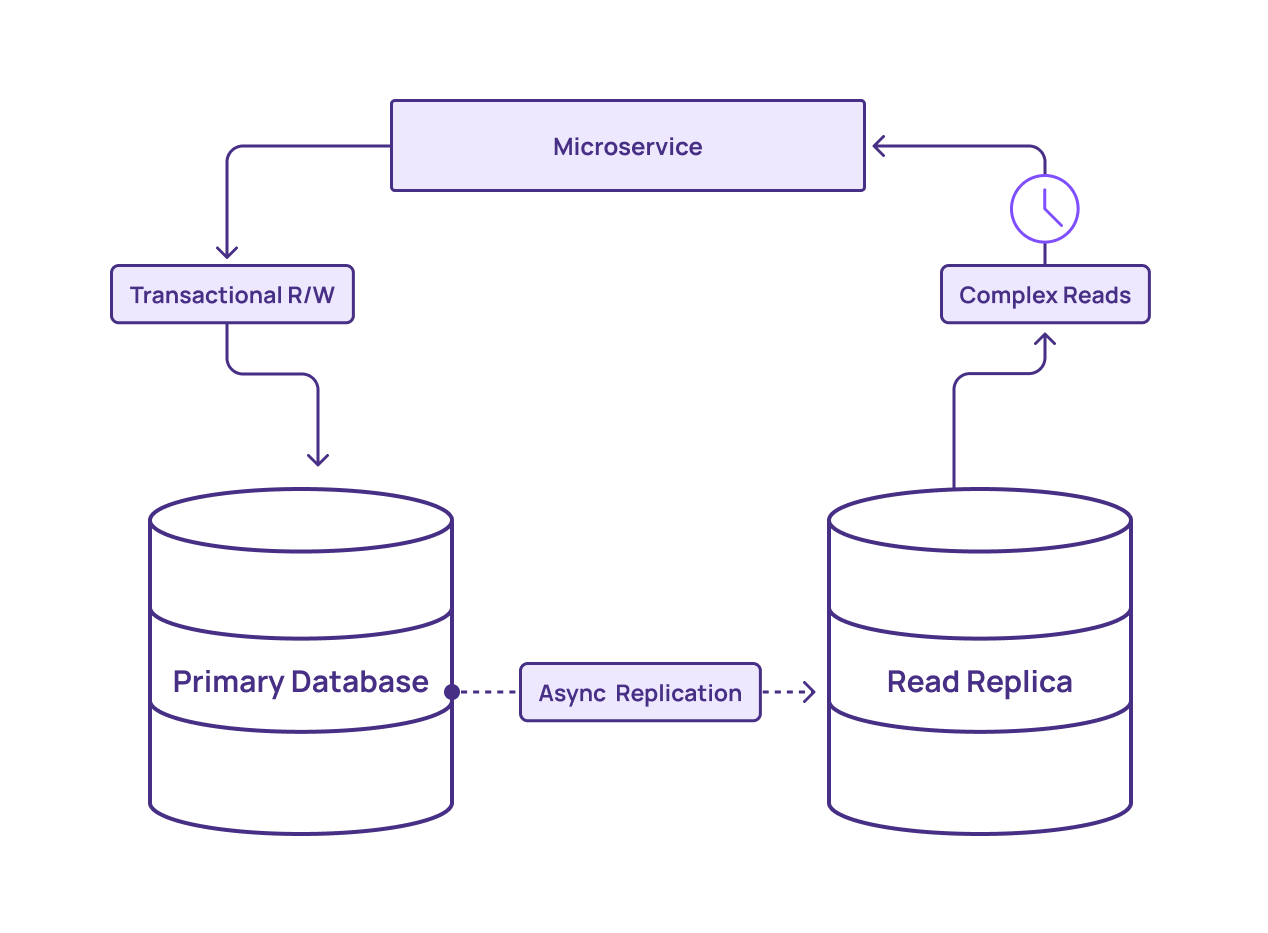
Internal Workflow
- User initiates a request (e.g., payment).
- Request reaches the transaction manager.
- Validation checks (schema, user permissions, input).
- SQL command is executed by the RDBMS.
- If all succeeds → COMMIT; if not → ROLLBACK.
- Transaction log updated, event published to monitoring tools.
Architecture Diagram (Descriptive)
[ Client Request ]
↓
[ Application Layer ]
↓
[ Transaction Manager ]
↙ ↘
[ Logging ] [ RDBMS Engine ]
↓
[ Storage + Audit Logs ]
Integration Points with CI/CD or Cloud Tools
- CI/CD Integration:
- Liquibase/Flyway for schema versioning
- pgTAP for SQL unit tests
- Cloud-native Tools:
- Amazon RDS, Google Cloud SQL (managed OLTP backends)
- Kubernetes StatefulSets with PostgreSQL
- Monitoring/Alerting:
- Prometheus/Grafana for DB metrics
- Falco/Sysdig for anomaly detection
4. Installation & Getting Started
Basic Setup or Prerequisites
- PostgreSQL or MySQL installed
- Docker and Docker Compose (for containerized OLTP setup)
- Basic SQL knowledge
Step-by-Step Beginner-Friendly Setup Guide
Using PostgreSQL + Docker
# docker-compose.yml
version: '3'
services:
postgres:
image: postgres:14
restart: always
environment:
POSTGRES_USER: devsecops
POSTGRES_PASSWORD: securepass
POSTGRES_DB: devsecopsdb
ports:
- "5432:5432"
# Start the OLTP service
docker-compose up -d
Connect and Run OLTP Transactions
psql -h localhost -U devsecops -d devsecopsdb
-- Create a sample transactional table
CREATE TABLE payments (
id SERIAL PRIMARY KEY,
user_id INT,
amount DECIMAL,
status VARCHAR(10),
created_at TIMESTAMP DEFAULT CURRENT_TIMESTAMP
);
-- Insert a transaction
BEGIN;
INSERT INTO payments (user_id, amount, status) VALUES (1, 250.00, 'PENDING');
COMMIT;
5. Real-World Use Cases
DevSecOps Scenario 1: CI/CD Audit Logging
- Every pipeline event (build, deploy) is logged as a transaction.
- Stored in an OLTP table for traceability and compliance audits.
DevSecOps Scenario 2: Secrets and Key Rotation
- When a secret is updated, a transaction logs:
- Old value reference (hashed)
- Timestamp
- Rotated status
DevSecOps Scenario 3: Real-Time Alerting
- Alert events from Falco/ZAP are recorded in an OLTP DB.
- Enables real-time dashboards and escalation triggers.
DevSecOps Scenario 4: Compliance Checks
- OLTP stores evidence of user access logs, configuration changes.
- Enables audit trail necessary for standards like SOC2, ISO 27001.
6. Benefits & Limitations
Key Advantages
- High Throughput: Supports thousands of transactions per second.
- Data Integrity: ACID compliance ensures consistent state.
- Auditability: Complete trace of every transaction.
- Real-time Updates: Suitable for operational monitoring systems.
Common Challenges
- Scalability: Vertical scaling often needed (vs. OLAP).
- Complex Schema Management: Requires rigorous version control.
- Lock Contention: High concurrency can lead to blocking or deadlocks.
- Not Optimized for Analytics: Poor for complex queries across big data.
7. Best Practices & Recommendations
Security Tips
- Use role-based access control (RBAC) on transaction tables.
- Enable SSL encryption for data in transit.
- Implement parameterized queries to prevent SQL injection.
Performance
- Use connection pooling (e.g., PgBouncer).
- Tune indexes based on frequent queries.
- Schedule vacuuming (PostgreSQL) for performance optimization.
Maintenance
- Backup using
pg_dump, automate daily. - Monitor disk usage, query performance (via Grafana dashboards).
Compliance & Automation
- Integrate with HashiCorp Vault or AWS Secrets Manager.
- Use Liquibase in CI/CD for version-controlled schema changes.
8. Comparison with Alternatives
| Feature | OLTP | OLAP | Time-Series DB (e.g., InfluxDB) |
|---|---|---|---|
| Optimized For | Transactions | Analytics | Time-based event storage |
| ACID Compliance | Yes | Sometimes | Not guaranteed |
| Use in DevSecOps | CI/CD, Audit | Reports | Monitoring/telemetry |
| Real-time Ops | Excellent | Poor | Excellent |
When to Choose OLTP Over Others
- You need ACID-compliant real-time audit logging.
- You require rollback capabilities for data integrity.
- Your DevSecOps processes depend on transactional control (e.g., access logging, payment authorization).
9. Conclusion
OLTP systems are fundamental to the security, traceability, and integrity of modern DevSecOps pipelines. Whether managing audit trails, secure secrets rotation, or compliance data, OLTP offers a transactional backbone that supports real-time responsiveness and reliability.
Future Trends
- Serverless OLTP: Integration with AWS Aurora Serverless.
- Distributed OLTP: Use of YugabyteDB, CockroachDB for horizontal scaling.
- AI-powered Index Tuning: Smart indexing via ML.
Official Resources
- PostgreSQL: https://www.postgresql.org/docs/
- MySQL: https://dev.mysql.com/doc/
- CockroachDB: https://www.cockroachlabs.com/docs/
- Liquibase: https://www.liquibase.org/