1. Introduction & Overview
What is a Semantic Layer?
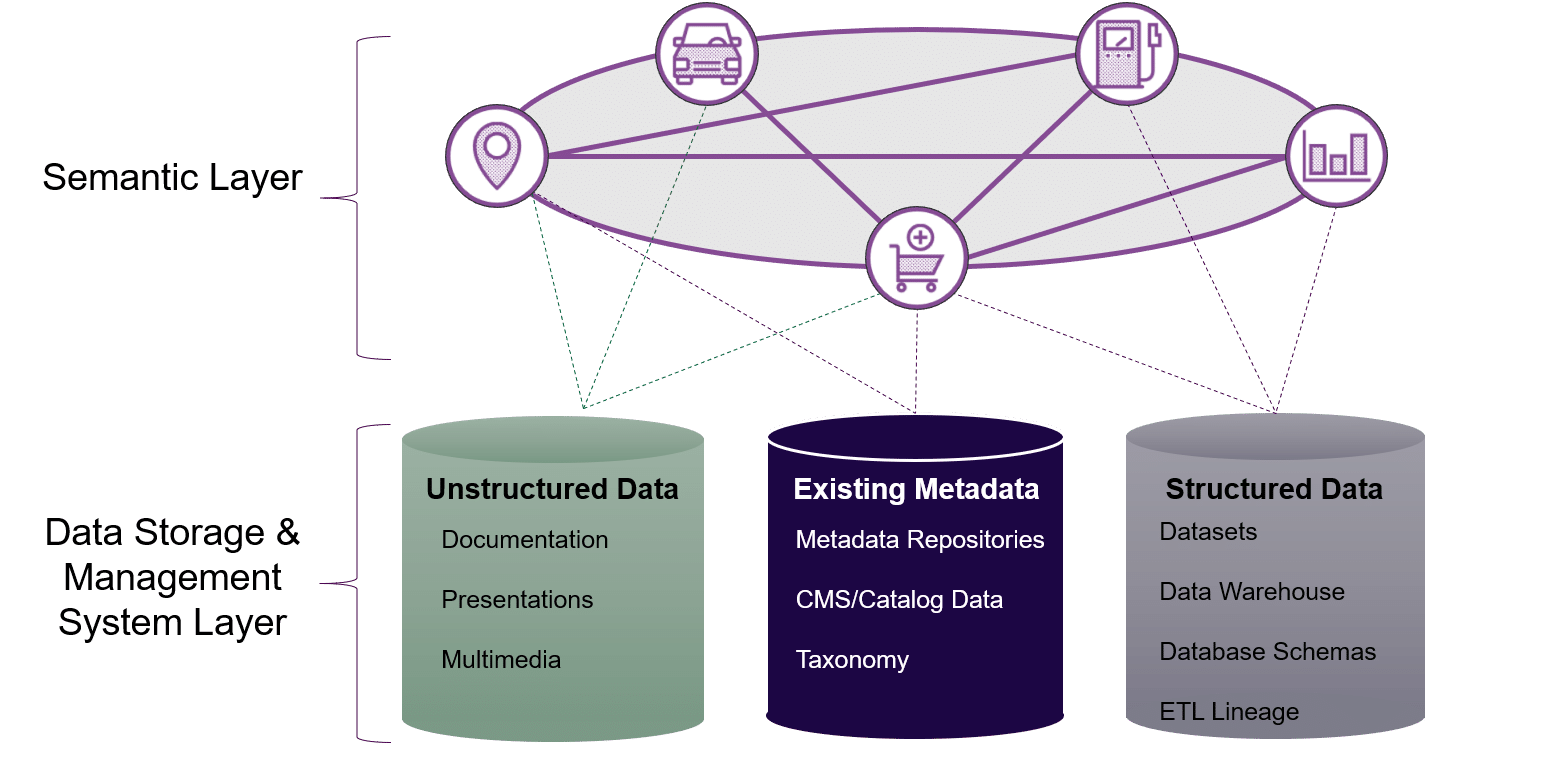
A Semantic Layer is an abstraction layer that sits between raw data sources and end users or applications. It translates complex data structures into user-friendly, consistent business terms—effectively decoupling backend technical implementation from frontend consumption.

In the context of DevSecOps, a Semantic Layer facilitates secure, governed, and consistent data access across CI/CD pipelines, analytics platforms, monitoring systems, and security dashboards.
History or Background
- Originated in the Business Intelligence (BI) space to empower non-technical users with self-service data access.
- Gained traction in data engineering and data mesh architectures for standardizing data access.
- Now extended to DevSecOps to align development, security, and operations using shared semantics for observability, security metadata, and policy enforcement.
Why is it Relevant in DevSecOps?
- Reduces risk of data misinterpretation across security and compliance tools.
- Ensures consistent metric definitions for alerts, audits, and SLOs.
- Promotes reusability and automation of policy enforcement and anomaly detection logic.
- Strengthens governance and traceability of how data is accessed and interpreted.
2. Core Concepts & Terminology
Key Terms and Definitions
| Term | Definition |
|---|---|
| Semantic Layer | Abstraction layer for translating technical data into business context. |
| Metric Layer | Defines KPIs, security rules, and metrics consistently. |
| Logical Model | Structured definitions of entities, relationships, and hierarchies. |
| Policy-as-Code | Encoding access rules and data policies into code. |
| Data Contract | Agreement between data producers and consumers on data format and meaning. |
How It Fits into the DevSecOps Lifecycle
| Stage | Role of Semantic Layer |
|---|---|
| Plan | Define consistent business logic for security and compliance metrics. |
| Develop | Enable developers to reference consistent definitions in unit/integration tests. |
| Build | Enrich CI/CD pipelines with security-aware semantic logic. |
| Test | Apply policy-as-code validation using consistent data definitions. |
| Release | Prevent deployment if semantic checks or contracts fail. |
| Deploy | Provide consistent monitoring metrics via observability pipelines. |
| Operate | Enable secure data exploration for ops teams using abstracted models. |
| Monitor | Use unified semantic models to generate accurate alerts and reports. |
3. Architecture & How It Works
Components
- Data Sources: Logs, telemetry, vulnerabilities, code repositories.
- Semantic Layer Engine: Central layer that maps source data to unified terms.
- Policy Engine: Validates access rules, metric rules, and policy-as-code.
- Consumers: Dashboards, alerting tools, security scanners, CI/CD pipelines.
Internal Workflow
- Data Ingestion: Ingests raw logs, metrics, code scan outputs, etc.
- Mapping Layer: Maps raw data fields to meaningful terms (e.g., “P1 vulnerability”, “Non-compliant IAM role”).
- Policy Enforcement: Validates incoming data against semantic rules.
- Query Serving: Makes clean, normalized data available to dashboards and DevSecOps tools.
Architecture Diagram (Descriptive)
┌────────────────────────────────────────────┐
│ DevSecOps Tools │
│ (CI/CD, Monitoring, Compliance Dashboards) │
└────────────────────────────────────────────┘
▲ ▲
│ │
┌─────────────┴─────────────┐
│ Semantic Layer │
│ - Metric Definitions │
│ - Data Contracts │
│ - Policy-as-Code Rules │
└─────────────▲─────────────┘
│
┌──────────────────────┼────────────────────────┐
│ │ │
┌──────────────┐ ┌────────────────┐ ┌────────────────┐
│ Vulnerability│ │ Audit Logs │ │ Cloud Metadata │
│ Scanners │ │ (SIEM, Syslog) │ │ (IAM, S3, etc) │
└──────────────┘ └────────────────┘ └────────────────┘
Integration Points with CI/CD or Cloud Tools
- GitHub Actions/GitLab CI: Validate data contracts in pre-deploy stages.
- AWS/GCP IAM: Enforce consistent definitions for policy violations.
- Datadog, Prometheus: Surface metrics with semantic labels.
- OPA/Rego: Use semantic logic to define access policies dynamically.
4. Installation & Getting Started
Basic Setup or Prerequisites
- Python/Node.js (depending on implementation)
- Docker (for container-based semantic services)
- YAML or JSON config knowledge
- Access to source systems: logs, CI/CD pipelines, cloud providers
Hands-on: Step-by-step Beginner-friendly Setup Guide
Let’s assume we’re using Transform (a popular open-source semantic layer):
- Install CLI
pip install transform-cli2. Initialize Project
transform init my-semantic-model
cd my-semantic-model3. Define a Metric
metrics:
high_risk_vulnerabilities:
description: "Count of P1 vulnerabilities in prod"
type: count
filter: severity = 'P1' AND environment = 'prod'
source: vulnerability_logs4. Serve API Locally
transform start5. Query the Metric
curl http://localhost:8080/metrics/high_risk_vulnerabilities5. Real-World Use Cases
1. CI/CD Pipeline Validation
- Scenario: Before deployment, run semantic checks on IaC scans to ensure there are no critical misconfigurations.
- Tooling: Terraform + Semantic Layer + GitHub Actions.
2. Unified Security Monitoring
- Scenario: Aggregate data from different tools (e.g., Snyk, Aqua) and normalize findings.
- Benefit: Reduce false positives with unified definitions.
3. Compliance Reporting
- Scenario: Automatically produce GDPR or SOC 2 reports using semantic definitions.
- Outcome: Consistent, auditable, and automated compliance dashboards.
4. Incident Response Enrichment
- Scenario: During an incident, auto-tag events using the semantic model (e.g., classify breach severity).
- Integration: SIEM → Semantic Layer → Incident Management System (PagerDuty, OpsGenie).
6. Benefits & Limitations
Key Advantages
- ✅ Consistency across teams
- ✅ Governed, secure access to critical metrics
- ✅ Faster time to insights
- ✅ Scalable and extensible definitions
- ✅ Automation-friendly
Common Challenges or Limitations
- ❌ Requires data modeling expertise
- ❌ May introduce latency in real-time pipelines
- ❌ Can become bottleneck if not decentralized properly
- ❌ Steep learning curve for small teams
7. Best Practices & Recommendations
Security Tips
- Use RBAC to control access to semantic definitions.
- Encrypt config files and secrets.
- Version-control all definitions in Git.
Performance
- Cache commonly used queries.
- Optimize backend SQL or API queries mapped in semantic layer.
Maintenance
- Set up CI tests to validate semantic logic.
- Maintain a data contract registry.
Compliance & Automation
- Integrate with OPA or Kyverno for policy validation.
- Use semantic metrics as triggers for alerting or remediation.
8. Comparison with Alternatives
| Feature | Semantic Layer | Hardcoded Logic | Data Warehouse Views |
|---|---|---|---|
| Decouples logic from storage | ✅ | ❌ | ❌ |
| Reusable across tools | ✅ | ❌ | ❌ |
| Governed and auditable | ✅ | ❌ | ✅ |
| Dynamic and programmable | ✅ | ❌ | ❌ |
| Real-time updates possible | ✅ | ✅ | ❌ |
When to Choose Semantic Layer
- Multiple DevSecOps tools need to share definitions
- High compliance or security visibility is needed
- You require policy enforcement + observability + analytics consistency
9. Conclusion
Semantic Layers represent a transformational shift in how teams approach data-driven DevSecOps. By aligning development, security, and operations teams with a shared language, organizations improve collaboration, security posture, and compliance readiness.
Next Steps
- Explore tools like Transform, Looker’s Semantic Layer, and dbt Semantic Layer.
- Join communities like: