Introduction & Overview
What is OLAP?
OLAP (Online Analytical Processing) refers to a category of tools and technologies that enable users to analyze large volumes of multidimensional data interactively and rapidly. It supports complex analytical queries, reporting, data mining, and business intelligence (BI) by organizing data in cubes rather than traditional flat tables.
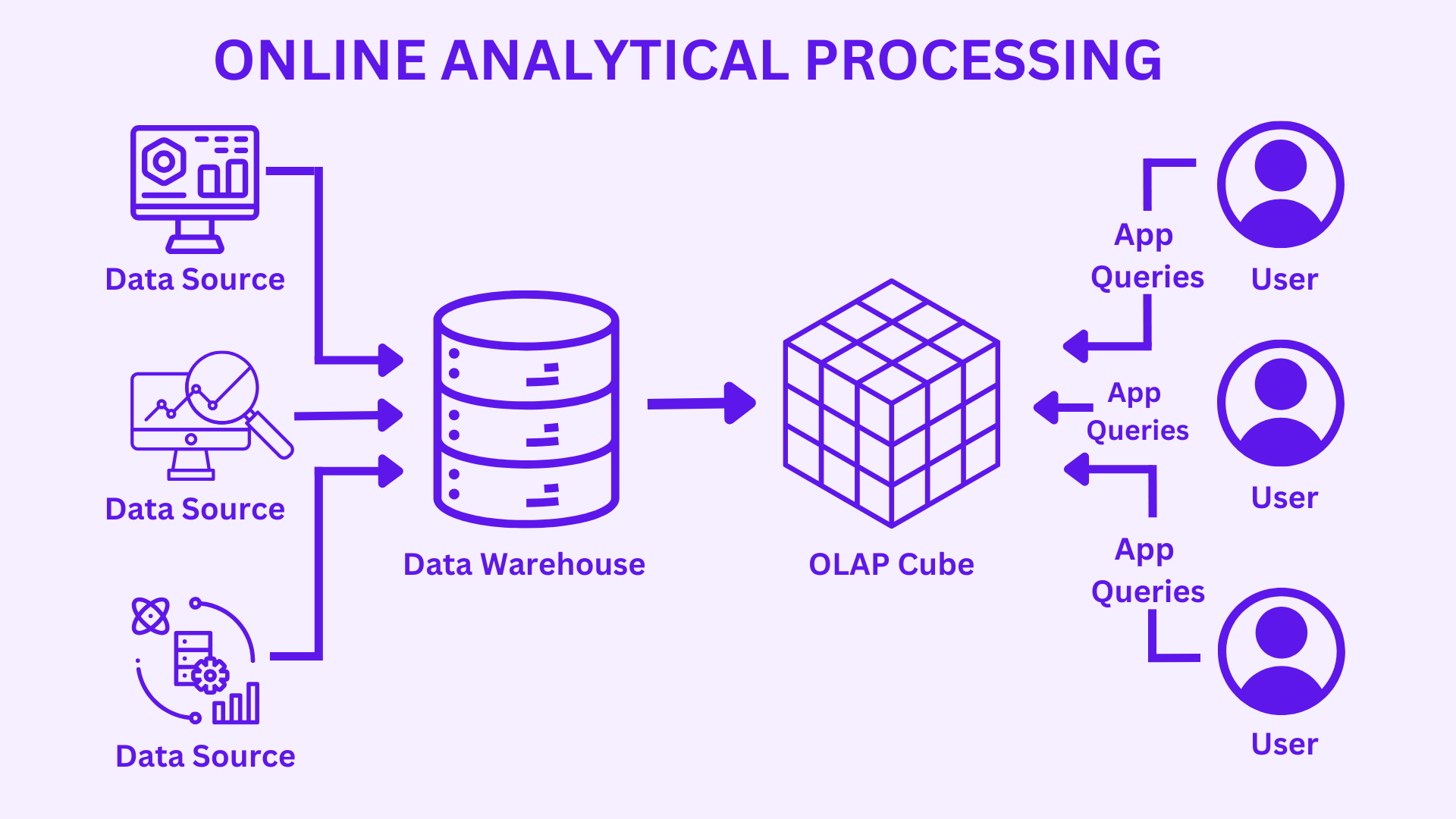
In DevSecOps, OLAP is used to analyze security, compliance, operations, and development data at scale to uncover insights for risk reduction, compliance tracking, and performance optimization.
History or Background
- 1993: Term coined by Edgar F. Codd to describe data analysis systems.
- Early 2000s: OLAP becomes integral to enterprise BI tools (e.g., Microsoft Analysis Services, Oracle OLAP).
- Modern Day: Evolved to support cloud-native platforms, security analytics, and real-time DevSecOps metrics.
Why is it Relevant in DevSecOps?
- Aggregates security and compliance data across CI/CD pipelines.
- Enables detection of anomalous trends or policy violations.
- Helps visualize infrastructure metrics, such as access logs, build failures, and policy drift.
- Supports regulatory audits (e.g., SOC 2, ISO 27001) through structured reporting.
Core Concepts & Terminology
Key Terms and Definitions
| Term | Definition |
|---|---|
| Cube | A multidimensional array of data used for slicing, dicing, and pivoting. |
| Dimension | A categorical axis of analysis (e.g., time, location, team). |
| Measure | Numeric data (e.g., login count, failed builds) analyzed across dimensions. |
| Drill-Down | Zooming in to explore detailed levels of data (e.g., from org → repo → user). |
| ETL | Extract, Transform, Load pipeline that feeds OLAP with clean data. |
| ROLAP/MOLAP | Relational or Multidimensional OLAP architectures. |
How it Fits into the DevSecOps Lifecycle
| DevSecOps Phase | OLAP Role |
|---|---|
| Plan | Analyze historical trends to inform secure design. |
| Develop | Identify frequent insecure coding patterns. |
| Build | Track failed security scans or policy violations. |
| Test | Analyze security testing coverage and results. |
| Release | Validate that releases meet compliance standards. |
| Deploy | Monitor deployment anomalies (e.g., unauthorized changes). |
| Operate | Track real-time metrics and incident patterns. |
| Monitor | Feed dashboards with aggregated metrics for ongoing observability. |
🏗️ Architecture & How It Works
Components & Internal Workflow
- Data Sources: CI/CD logs, SIEM tools, vulnerability scanners (e.g., Snyk, SonarQube).
- ETL Pipeline: Ingests and normalizes structured/unstructured data.
- OLAP Engine: Organizes data into cubes for high-performance querying.
- Query Layer: Enables interactive queries via SQL or OLAP-specific languages (e.g., MDX).
- BI Tools: Dashboards for visual exploration (e.g., Metabase, Superset, Power BI).

Architecture Diagram (Text Description)
[ CI/CD Logs ] [ Sec Tools ] [ Infra Metrics ]
↓ ↓ ↓
[ ETL Pipeline (Airflow/Fivetran) ]
↓
[ OLAP Engine (e.g., Apache Druid, ClickHouse) ]
↓
[ BI Tools / Dashboards / Alert Systems ]
Integration Points with CI/CD or Cloud Tools
| Tool | Integration Use Case |
|---|---|
| Jenkins/GitHub Actions | Ingest build logs and scan reports for OLAP analysis. |
| Kubernetes | Analyze pod security events, usage patterns. |
| AWS/GCP/Azure | Feed IAM logs, GuardDuty alerts into OLAP cubes. |
| SIEMs (e.g., Splunk) | Serve as upstream ETL sources for DevSecOps dashboards. |
🚀 Installation & Getting Started
Basic Setup or Prerequisites
- Linux/macOS system with Docker or Kubernetes
- Python/SQL skills
- Cloud-native ETL tools (optional): dbt, Airbyte, Apache NiFi
- Choose an OLAP engine:
- Apache Druid (real-time)
- ClickHouse (fast analytics)
- Cube.js (API-first)
Hands-On: Step-by-Step Setup with Apache Druid
Step 1: Clone & Launch Druid with Docker
git clone https://github.com/apache/druid.git
cd druid/distribution/docker
docker compose up
Step 2: Ingest Sample Data
curl -X POST -H 'Content-Type: application/json' -d @quickstart/tutorial/wikipedia-index.json \
http://localhost:8081/druid/indexer/v1/task
Step 3: Query via SQL
SELECT page, COUNT(*) as edits
FROM wikipedia
WHERE user IS NOT NULL
GROUP BY page
ORDER BY edits DESC
LIMIT 10;
Step 4: Connect BI Tool (e.g., Superset)
# Use Superset UI to connect via JDBC/HTTP to Druid
🔍 Real-World Use Cases
1. Vulnerability Tracking Across Pipelines
- Combine Snyk or Trivy scan logs.
- OLAP cube shows frequency and severity per repo/team.
- Helps prioritize refactoring efforts.
2. Compliance Monitoring
- Ingest IAM logs and Kubernetes audit trails.
- Identify non-compliant user access patterns over time.
3. Code Quality Metrics
- Use SonarQube output + git commit history.
- Drill down by project, author, or team.
4. Incident Forensics
- Combine real-time logs with past deployment metrics.
- Enables root-cause analysis of security breaches.
✅ Benefits & Limitations
Key Advantages
- 📈 High-performance analytics even on large datasets.
- 🔁 Multidimensional slicing/dicing for deep insights.
- 🤝 Integrates well with modern DevSecOps and BI tools.
- ⚡ Real-time ingestion enables proactive alerts.
Common Challenges
- 🛠️ Complex setup for distributed OLAP engines.
- 📦 High storage and compute cost for large cubes.
- 🔍 Requires good data modeling to be effective.
- 🧱 Not ideal for transactional (row-based) queries.
🔒 Best Practices & Recommendations
Security Tips
- Use encryption at rest and in transit for sensitive logs.
- Implement RBAC on OLAP dashboards.
- Sanitize data during ETL to remove PII.
Performance
- Optimize with pre-aggregations and partitioning.
- Offload raw storage to data lakes (e.g., S3).
Maintenance
- Automate ETL job retries and monitor latency.
- Archive old cubes to reduce cost.
Compliance & Automation
- Auto-generate audit dashboards.
- Integrate with tools like OPA (Open Policy Agent) to flag policy violations.
- Export reports for SOC 2, PCI-DSS evidence collection.
🔄 Comparison with Alternatives
| Feature | OLAP Engines | SQL DBs | Time-Series DBs |
|---|---|---|---|
| Multidimensional | ✅ Yes | ❌ No | ❌ No |
| Real-time Query | ⚠️ Limited (depends) | ✅ Some | ✅ Yes |
| DevSecOps Fit | ✅ High | ⚠️ Medium | ✅ High (metrics) |
| Storage Footprint | ⚠️ High | ✅ Efficient | ✅ Efficient |
When to Choose OLAP?
Choose OLAP over traditional tools when:
- You need complex cross-dimensional queries.
- Your data spans multiple DevSecOps pipelines.
- You require dashboards for auditors, CISOs, or engineering leaders.
🧭 Conclusion
OLAP is a powerful enabler of visibility, security analytics, and compliance in modern DevSecOps environments. It integrates deeply with CI/CD tools, cloud platforms, and security solutions to deliver real-time, multi-dimensional insights.
As DevSecOps maturity evolves, integrating OLAP into observability, governance, and response pipelines will become standard practice
📎 Further Reading & Resources
- 🔗 Apache Druid Docs
- 🔗 ClickHouse Docs
- 🔗 Cube.js DevSecOps Examples
- 🔗 Awesome OLAP GitHub Repo
- 🔗 CNCF Security Landscape