
1. Introduction & Overview
What is Snowflake?
Snowflake is a cloud-native data warehousing and analytics platform that supports data storage, processing, and analysis. Built on top of Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP), Snowflake allows users to store and analyze data using scalable, distributed compute and storage layers.

It is especially well-suited for modern applications that require elasticity, performance, and security in the cloud. In the DevSecOps landscape, Snowflake plays a pivotal role in secure data analytics, compliance monitoring, threat intelligence, and operational insights.
History or Background
- Founded: 2012 by Benoit Dageville, Thierry Cruanes, and Marcin Żukowski
- Public Offering: IPO in 2020, symbol SNOW
- Initial Objective: To overcome the limitations of traditional data warehouses using a cloud-native architecture
- Current Status: Leading cloud data platform used by companies like Adobe, Capital One, and Allianz
Why is it Relevant in DevSecOps?
DevSecOps integrates security practices into the DevOps lifecycle. Snowflake aids this through:
- Data Governance & Compliance: GDPR, HIPAA, SOC 2 compliance support
- Security Data Lake: Aggregating and analyzing logs from various security tools
- Anomaly Detection: Behavioral analytics using large datasets
- Audit Trails: Track user activity and ensure accountability
2. Core Concepts & Terminology
Key Terms and Definitions
| Term | Definition |
|---|---|
| Warehouse | Virtual compute cluster used to execute queries |
| Database | Logical container for schemas and tables |
| Schema | Structure organizing tables, views, and procedures |
| Role-Based Access Control (RBAC) | Granular permission model to enforce least privilege |
| Snowpipe | Continuous data ingestion pipeline from cloud storage |
| Time Travel | Feature to access historical data changes |
| Secure Views | Obfuscates sensitive data for secure analytics |
How it Fits into the DevSecOps Lifecycle
| DevSecOps Phase | Snowflake Role |
|---|---|
| Plan | Data-driven threat modeling using historical logs |
| Develop | Usage analytics on developer patterns |
| Build | CI/CD pipeline audit and compliance checks |
| Test | Correlating test failures with production data |
| Release | Release-based metrics and quality gates |
| Deploy | Monitoring misconfigurations via security telemetry |
| Operate | Real-time dashboard for infrastructure and application observability |
| Monitor | Ingest logs for threat detection and behavioral anomaly detection |
3. Architecture & How It Works
Components and Internal Workflow
Snowflake operates on a multi-cluster shared data architecture, which separates compute, storage, and services.
- Cloud Services Layer:
- Handles authentication, metadata, access control
- Query Processing Layer (Virtual Warehouses):
- Runs SQL queries using on-demand compute clusters
- Storage Layer:
- Stores structured and semi-structured data in a compressed columnar format
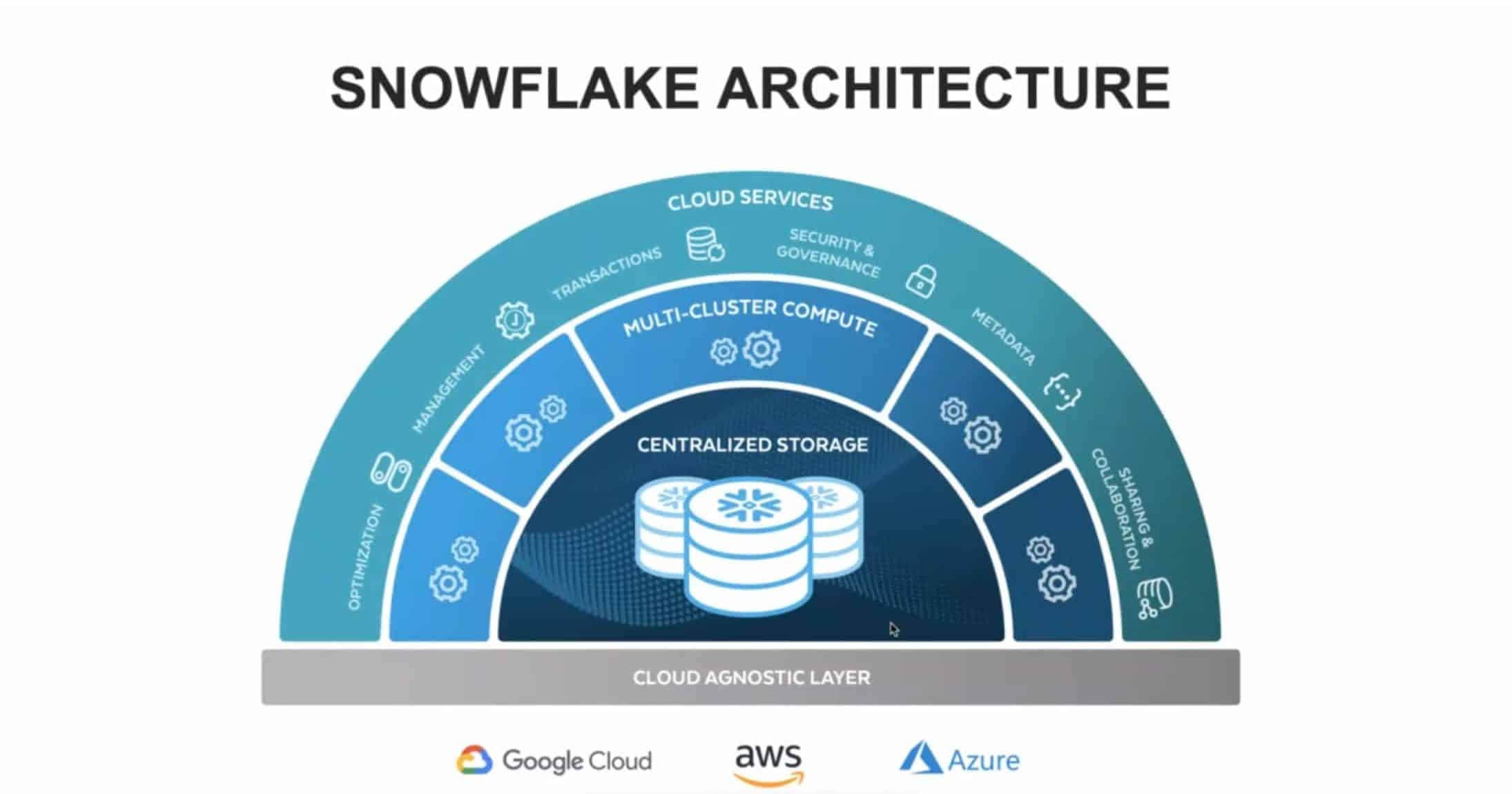
Architecture Diagram (Textual Description)
+----------------------+
| DevSecOps Tools |
| (SIEM, CI/CD, etc.) |
+----------+-----------+
|
+---------v---------+
| Snowpipe / API | <-- Data ingestion layer
+---------+---------+
|
+---------v----------+
| Storage Layer | <-- Stores log, app, infra data
+---------+----------+
|
+---------v----------+
| Compute Warehouses | <-- Parallel query processing
+---------+----------+
|
+---------v----------+
| Cloud Services | <-- Access, metadata, RBAC
+-------------------+
Integration Points with CI/CD or Cloud Tools
- CI/CD: Export pipeline logs (e.g., GitHub Actions, Jenkins) → store in Snowflake via Snowpipe
- Cloud Platforms:
- AWS/GCP/Azure: Native support for object storage ingestion (e.g., S3 → Snowflake)
- Security Tools:
- Ingest logs from Falco, ZAP, or SonarQube for real-time analytics
- Observability:
- Integrated with Datadog, Splunk, or Prometheus through data connectors
4. Installation & Getting Started
Basic Setup or Prerequisites
- Cloud account (AWS, GCP, or Azure)
- Snowflake trial account: https://signup.snowflake.com/
- CLI: SnowSQL
- Optional: Python with
snowflake-connector-python
Hands-on: Beginner-Friendly Setup Guide
- Create Snowflake Account
- Visit https://signup.snowflake.com/
- Choose cloud provider and region
- Set Up Database and Warehouse
CREATE WAREHOUSE devops_wh;
CREATE DATABASE devops_db;
CREATE SCHEMA security_logs;3. Create Role and User
CREATE ROLE devsecops_analyst;
GRANT USAGE ON WAREHOUSE devops_wh TO ROLE devsecops_analyst;
CREATE USER analyst PASSWORD='Secure123!';
GRANT ROLE devsecops_analyst TO USER analyst;4. Ingest Sample Data
- Upload CI/CD or system logs to S3
- Create external stage:
CREATE STAGE log_stage
URL='s3://my-logs-bucket'
CREDENTIALS=(AWS_KEY_ID='...' AWS_SECRET_KEY='...');
5. Query Logs
SELECT * FROM security_logs.cicd_audit WHERE status = 'failed';5. Real-World Use Cases
Use Case 1: CI/CD Pipeline Analytics
- Ingest Jenkins or GitHub Actions logs into Snowflake
- Identify recurring build failures
- Detect unusual user behaviors
Use Case 2: Threat Intelligence Correlation
- Combine logs from WAFs, IDS (e.g., Suricata) with application logs
- Perform correlation and detect lateral movement
Use Case 3: Regulatory Compliance
- Use Snowflake’s Time Travel for audit trails
- Automate checks against HIPAA, SOC 2 policies
Use Case 4: Insider Threat Detection
- Monitor usage patterns and access logs
- Flag abnormal behavior using custom queries or machine learning integrations
6. Benefits & Limitations
Key Advantages
- Scalability: Independent scaling of compute and storage
- Security: End-to-end encryption, SSO, RBAC, data masking
- Multi-Cloud: Seamless across AWS, Azure, and GCP
- Time Travel: Rewind and recover historical data
- Built-in Governance: Tags, policies, and access control
Common Challenges
- Cost Predictability: On-demand compute can incur unexpected costs
- Latency for Real-Time Ingestion: Slight lag in streaming ingestion
- Vendor Lock-in: Proprietary features reduce portability
- Learning Curve: Non-SQL-native users may need onboarding time
7. Best Practices & Recommendations
Security Tips
- Enforce MFA and SSO using identity providers
- Use Network Policies to whitelist IPs
- Apply dynamic data masking for sensitive fields
Performance Optimization
- Use clustering keys on large tables
- Leverage materialized views for frequently used queries
- Auto-scale warehouses based on demand
Compliance Alignment
- Use Object Tagging for regulatory classification
- Automate data retention policies
- Periodic access review of roles and users
Automation Ideas
- Automate data ingestion using Snowpipe + Event Triggers
- Monitor security posture using SQL-based dashboards
- Set up alerts with webhooks or integrations
8. Comparison with Alternatives
| Feature | Snowflake | BigQuery | Redshift | Databricks |
|---|---|---|---|---|
| Storage & Compute | Separated | Separated | Tightly coupled | Separated |
| Security | Advanced RBAC, Masking | IAM + ACL | VPC-only | ACL + Encryption |
| Ease of Use | SQL-friendly | SQL-like | SQL-friendly | Python/Scala heavy |
| Best For | Compliance + Analytics | Ad-hoc BI | ETL-heavy apps | ML + data science |
| When to Use | Secure analytics, DevSecOps dashboards | Quick insights | High ETL throughput | ML-rich pipelines |
9. Conclusion
Snowflake is a strategic asset in the DevSecOps lifecycle, enabling data-driven security, governance, and automation. Its cloud-native, scalable, and secure architecture makes it ideal for modern development environments where data compliance and operational visibility are essential.
Future Trends
- Native AI/ML integration for predictive security
- Deeper integration with cloud-native DevSecOps pipelines
- Growth in data sharing for threat intelligence
Next Steps
- Explore the official documentation: https://docs.snowflake.com/
- Join the community: https://community.snowflake.com/
- Try Snowflake free: https://signup.snowflake.com/